How AI Phone Systems Ensure Secure Data Transmission
AI phone systems prioritize security to protect sensitive information shared during calls. These systems handle tasks like voice capture, transcription, and data storage, often processing confidential data such as payment details or personal information. To address security concerns, they use:
- End-to-end encryption: Protocols like SRTP and TLS secure audio and signaling data during transmission.
- Access controls: Role-Based Access Control (RBAC) and Multi-Factor Authentication (MFA) limit data access to authorized personnel.
- Regulatory compliance: Industries like healthcare and finance follow standards like HIPAA and PCI-DSS to safeguard sensitive data.
- Monitoring and response: Real-time tools and incident response frameworks detect and address potential breaches.
These measures not only protect data but also help businesses comply with industry regulations, avoid fines, and build trust with customers.
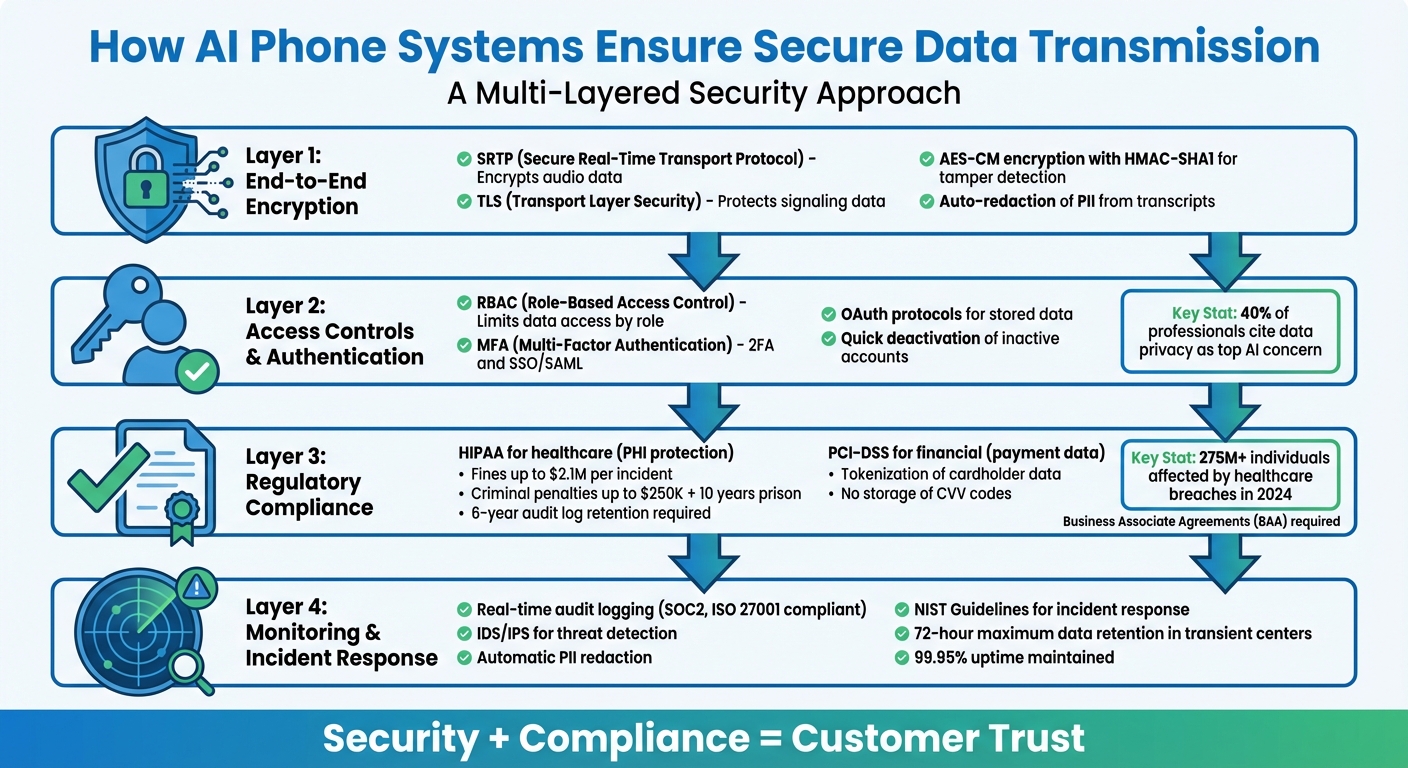
4 Security Layers in AI Phone Systems for Data Protection
Securing AI Systems: Protecting Data, Models, & Usage
How AI Phone Systems Protect Sensitive Data
AI phone systems use multiple layers of security to protect sensitive information during calls, aiming to prevent unauthorized access, interception, and misuse.
End-to-End Encryption for Data in Transit
When a customer interacts with an AI phone system, two encryption protocols work together to secure the communication. Secure Real-Time Transport Protocol (SRTP) encrypts the audio data, ensuring that intercepted voice information is unreadable. Meanwhile, Transport Layer Security (TLS) safeguards signaling data, such as caller names and phone numbers. Matt Coser, Senior Field Security Engineer at Twilio, highlights the importance of SRTP:
Using SRTP essentially renders sniffed packets useless, which mitigates the risk of data exposure the threat of eavesdropping poses.
SRTP typically relies on AES-CM encryption, offering strong protection with minimal processing demands. It also includes a replay window to block replay attacks and uses HMAC-SHA1 to detect tampering. Additionally, modern AI phone systems may incorporate machine learning tools to automatically redact personally identifiable information (PII) from call transcripts. In some cases, these systems can pause recording and transcription when sensitive transaction details are detected. These measures create a solid foundation for further access controls.
Role-Based Access Controls and Authentication
Encryption alone isn’t enough - controlling who can access stored data is equally critical. Role-Based Access Control (RBAC) ensures that only employees with a legitimate need can view sensitive information. For instance, a customer service agent might access call transcripts, but payment details remain off-limits.
To strengthen security, systems often implement Multi-Factor Authentication (MFA), which includes methods like Two-Factor Authentication (2FA) and Single Sign-On (SSO) using SAML. These tools require an additional verification step, ensuring only authorized users gain access. Detailed permissions and OAuth protocols offer even more safeguards for stored data.
This layered approach addresses growing concerns about data privacy, as 40% of professionals cite it as their top issue with AI. AI voice systems, which may inadvertently capture biometric or emotional signals, make these protections even more vital. Companies should also deactivate inactive accounts quickly and enforce strict data retention policies to reduce the risk of exposure.
Compliance with Industry Standards and Regulations
Meeting regulatory standards is a critical part of ensuring secure data transmission. Each industry has its own set of rules, and failing to comply can lead to severe consequences. For instance, in 2024, healthcare data breaches impacted more than 275 million individuals. These regulations work hand-in-hand with existing security measures, reinforcing a multi-layered approach to data protection.
HIPAA and PCI Compliance Standards
Healthcare providers using AI phone systems must adhere to the Health Insurance Portability and Accountability Act (HIPAA), which safeguards Protected Health Information (PHI). When an AI system records, transcribes, or analyzes patient calls, it directly handles electronic PHI (ePHI), triggering stringent security protocols [18,20]. Among these requirements is audit logging, which tracks every interaction with patient data and must be retained for at least six years.
The financial risks of noncompliance are steep. HIPAA violations can lead to fines of up to $2.1 million per incident. Intentional breaches, such as disclosing PHI without authorization, can result in criminal penalties of up to $250,000 and prison sentences of up to 10 years [18,22]. In 2022, HIPAA settlements for dental practices alone reached $305,500.
For businesses handling credit card payments, compliance with the PCI-DSS is mandatory. This standard prohibits storing Sensitive Authentication Data (SAD), like CVV codes, in call recordings or transcripts. To mitigate risks, many AI phone systems use tokenization, replacing sensitive cardholder data with non-sensitive tokens during transmission and storage. This approach aligns regulatory requirements with technical safeguards.
Business Associate Agreements and Vendor Responsibilities
A Business Associate Agreement (BAA) is a legal document that holds AI phone system vendors accountable for protecting PHI under HIPAA. Preston Thomas, Senior Privacy and Compliance Counsel at Dialpad, emphasizes the importance of this agreement:
If you're dealing with a VoIP provider that stores ePHI information for you and doesn't ask for a Business Associate Agreement, run! You could be faced with some serious penalties.
The BAA specifies how the vendor will secure patient data and outlines liability for any compliance breaches [18,20]. It also extends to subcontractors, such as cloud hosting providers or third-party AI services. Without a signed BAA, transmitting PHI through an AI phone system is a significant risk.
Modern BAAs often include clauses that forbid using PHI to train AI models without explicit permission. They also require vendors to maintain detailed audit logs, perform regular vulnerability scans, and undergo third-party audits like SOC 2 Type II to confirm the effectiveness of their security measures [16,18]. These agreements are typically reviewed every 12–24 months, especially when AI features like sentiment analysis or automated transcription are introduced.
sbb-itb-abfc69c
Monitoring and Incident Response Mechanisms
Continuous monitoring plays a key role in safeguarding data transmission within AI phone systems. While encryption and access controls are vital, the ability to detect and respond swiftly to threats is just as critical. These systems rely on monitoring tools and structured response protocols to spot unusual activity and address potential breaches before they escalate. Together, these tools and protocols bolster encryption and access measures, creating a strong security framework.
Audit Logging for Transparency and Accountability
Every interaction with the system is meticulously logged, recording details such as who accessed the data, when it was accessed, and what changes were made. This comprehensive record ensures accountability and helps businesses comply with regulations like SOC2 and ISO 27001.
This logging system not only deters insider misuse but also provides clear, verifiable documentation for audits. To further enhance security, Support Codes are required for identity verification during administrative changes, reducing the risk of unauthorized actions.
"Because our AI features and models are only as good as the real world data they are based on, the security and safety of customer data is fundamental to ethical data use."
- Preston Thomas, Senior Privacy and Compliance Counsel at Dialpad
Audit logs work seamlessly with role-based access controls, ensuring that only authorized individuals can access sensitive data. Every access attempt is recorded and traceable, providing an extra layer of security. These practices align with real-time threat detection, creating a comprehensive defense system.
Real-Time Monitoring and Incident Response
Modern AI phone systems are equipped to identify and counter threats as they happen. Tools like IDS/IPS continuously monitor network traffic, instantly blocking malicious activities. Rate-limiting mechanisms further protect against brute-force attacks by restricting suspicious traffic.
AI-driven tools also enhance security by performing automatic PII redaction, which identifies and removes sensitive information - such as Social Security numbers or credit card details - from call transcripts in real time. Additionally, security scanners are integrated into continuous integration (CI) pipelines, detecting vulnerabilities in new features before deployment.
If a security breach occurs, providers adhere to standardized frameworks like the NIST Guidelines for incident response, ensuring a swift and organized approach.
"Dialpad follows the NIST Guidelines for incident response. Per our Terms of Service and contractual obligations, Dialpad will notify customers of any breach involving their data."
- Dialpad
This process includes immediate containment, detailed investigation, and timely customer notification. Even during these events, some systems maintain 99.95% uptime, ensuring minimal disruption to business operations.
To limit exposure, transient customer data in certain data centers is retained for no more than 72 hours. Additionally, sessions for desktop and web applications automatically time out after 30 days, reducing the risk of unauthorized access from unattended devices.
Conclusion
Secure data transmission in AI phone systems isn't just about meeting regulations - it's about establishing trust. By using end-to-end encryption, role-based access controls, and continuous monitoring, businesses can create a strong, multi-layered defense against potential breaches. Encryption ensures that sensitive data, whether in transit or stored, remains unreadable even if intercepted. This approach not only helps prevent breaches but also supports compliance with critical standards.
Meeting regulations like HIPAA and PCI isn't optional. Beyond avoiding hefty penalties, adhering to these standards signals to enterprise clients that your phone system prioritizes security and reliability.
These measures go beyond compliance - they create a robust security framework that benefits everyone involved. Businesses that adopt these practices often see reduced risks and smoother operations as a result.
"Privacy-by-design... protects customers and demonstrates responsibility before regulators ask for it."
Data security doesn't just protect your business; it strengthens customer trust. Safeguarding sensitive information, staying compliant with industry standards, and prioritizing privacy can turn first-time users into loyal customers. With 40% of professionals identifying data privacy as their top concern regarding AI, implementing these measures isn't just smart - it's essential to staying ahead in a competitive landscape.
FAQs
How do AI phone systems protect conversations with end-to-end encryption?
End-to-end encryption locks down data shared during a call by encrypting it right at the source and only allowing decryption at its final destination. In simple terms, only the sender and receiver can see or hear the conversation, keeping it out of reach from third parties - even the service provider.
AI phone systems take this a step further by generating unique encryption keys for every call. This ensures sensitive information stays protected and blocks any unauthorized access while the data is being transmitted. It's a game-changer for businesses and customers who rely on secure and private communication.
What happens if a business doesn't comply with HIPAA or PCI standards?
Failing to meet HIPAA (Health Insurance Portability and Accountability Act) or PCI (Payment Card Industry) standards can lead to serious consequences. Businesses may face steep fines, legal repercussions, and long-term damage to their reputation - something that can take years to repair.
Beyond financial and legal risks, noncompliance significantly raises the chances of data breaches, exposing sensitive patient or payment information. Such incidents not only break customer trust but can also result in expensive lawsuits and disrupt day-to-day operations. Staying compliant is crucial for safeguarding both your business and the people who rely on you.
How do AI phone systems keep data secure and respond to threats in real time?
AI-powered phone systems play a crucial role in keeping communication secure. They continuously monitor call activity and use advanced behavioral analytics to spot anything unusual, like suspicious call patterns or unexpected voice changes. Once a potential threat is detected, the system can respond instantly by blocking the call, rerouting it, or notifying security teams.
These systems rely on machine learning and voice biometrics to identify and prevent risks such as voice spoofing, deepfakes, or unauthorized access attempts. Over time, they become more effective, using predictive models to tackle new security challenges as they arise. This real-time response ensures sensitive information stays protected and communication channels remain secure.
Related Blog Posts
Related Articles
Virtual Receptionist ROI: Long-Term Savings
Compare in-house vs virtual receptionists and learn how 24/7 AI services cut costs, recover missed-call revenue, and boost long-term ROI.
AI Call Answering for 24/7 Global Coverage
AI call answering revolutionizes customer service with 24/7 availability, cost savings, and improved customer satisfaction across time zones.
Ultimate Guide to AI Voice Consistency
A practical guide to define, tune, and monitor AI voice for consistent brand interactions—covering tone, personas, TTS settings, audits, accessibility, and ethics.
